April 16, 2024 Weekly Notification
April 16th, 2024
Every Tuesday we send out an email to every employee with information from the district This email...
Phishing is a cybercrime. It is received by email, phone, or text message from a cyber criminal pretending to be an organization/person that is legitimate. They lure you into giving up sensitive information such as passwords, bank/credit card information, or personally identifiable information. After they get this information, it’s used to gain access to your accounts, putting you at risk of identity theft and financial loss.
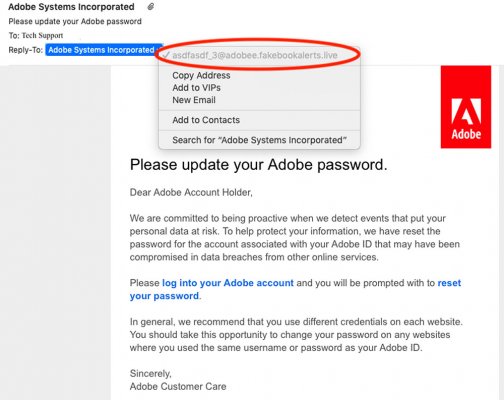
1. Looking at the sender’s email address, you can see that this is not from a valid adobe email address, but rather a “fakebookalerts.live” address. This should be the first warning that this is not a legitimate email since it’s talking about an adobe password change. Also if you look closely in this example the subdomain is “adobee” instead of “adobe”
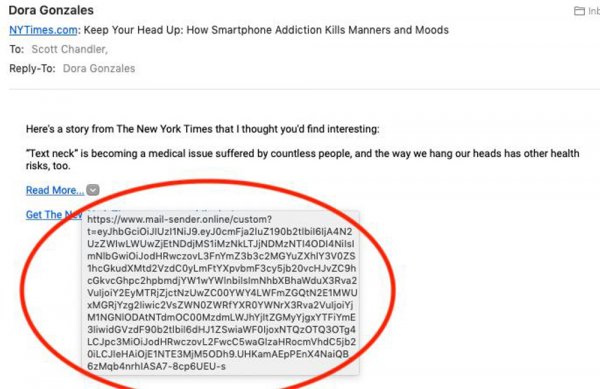
2. In this example, this link is not a part of the New York Times domain, but an external site at mail-sender.online. This should be another warning that this is not a legitimate email.
Every Tuesday we send out an email to every employee with information from the district This email...
Try This Strategy! Don’t Mention It This is a great strategy to help students review vocabulary...
This summer the technology department in conjunction with Google will perform a merger of the...
We would like to help you celebrate your retirees If you have individuals retiring from your...
Although it began in the United States in 1970, Earth Day is celebrated by more than 1 billion...
Do you want the latest STEM teaching tools in your classroom Then make sure you sign up for the...